Cybersecurity is no longer a luxury, but a necessity for businesses however, it’s common for security to be viewed as a cost center, which often leads to insufficient budgets and lackluster defenses. In this opinion piece, Cole Jackson who has worked with startups to Fortune 1000 as a vCISO and cybersecurity program strategist, explores the value-based approach to cybersecurity budgeting, which emphasizes the importance of linking security spending to direct monetary value earned or protected. The article outlines a step-by-step methodology for organizations to calculate the direct value added by their cybersecurity team, enabling them to pitch their budget requests with a compelling story backed by metrics. Enjoy reading!
Background – The Cost Center Trap
It’s well established that security is often seen as a cost center.
This way of thinking parallels how departments like accounting or HR are viewed; they spend money to make sure the books are well-maintained for forecasting, or ensuring that the business and its employees color within all the regulatory and cultural lines, respectively.
The perception is that the cost of doing business includes keeping the systems operational and safe so that the customers keep paying.
The issue, then, is determining exactly what costs and investments are warranted. If nothing went wrong in the last year, what is the incentive for upgrading systems, hiring more hands, or investing in third-party tooling or services?
This is the framework trap that I’ve personally seen many organizations fall into, and it exposes a backwards method of thinking, “How much money do we want to sink into this just to be able to do business?”
You Make The Money
Security can (and should be) seen as a potential revenue and value-earning center of the business.
The means by which this can happen are numerous, but here are the specific cases I have personally encountered:
- The security team has helped implement incident response processes and techniques that turned a subsequent ransomware threat into a minor incident with zero customer impact. This means that stress was kept low, man hours potentially lost to the incident were protected, revenue-generating services were kept online, and customer brand damage was avoided. We calculated this after the fact and attributed it to specific actions and budgetary items.
- The security team worked to implement a set of control and process integrations from a compliance framework that dozens of customers were going to start demanding in the coming year. By achieving certification in the framework, the company was able to win $9.4m TCV (Total Contract Value) of business, as well as follow-on marketing benefits.
What is the key variable for flipping the “cost-center” framework to the “value-add” budget approach?
Attach everything you do to a dollar amount earned or a dollar amount protected.
However, getting there requires telling a good story, backed by metrics.
Get out a piece of paper and a calculator.
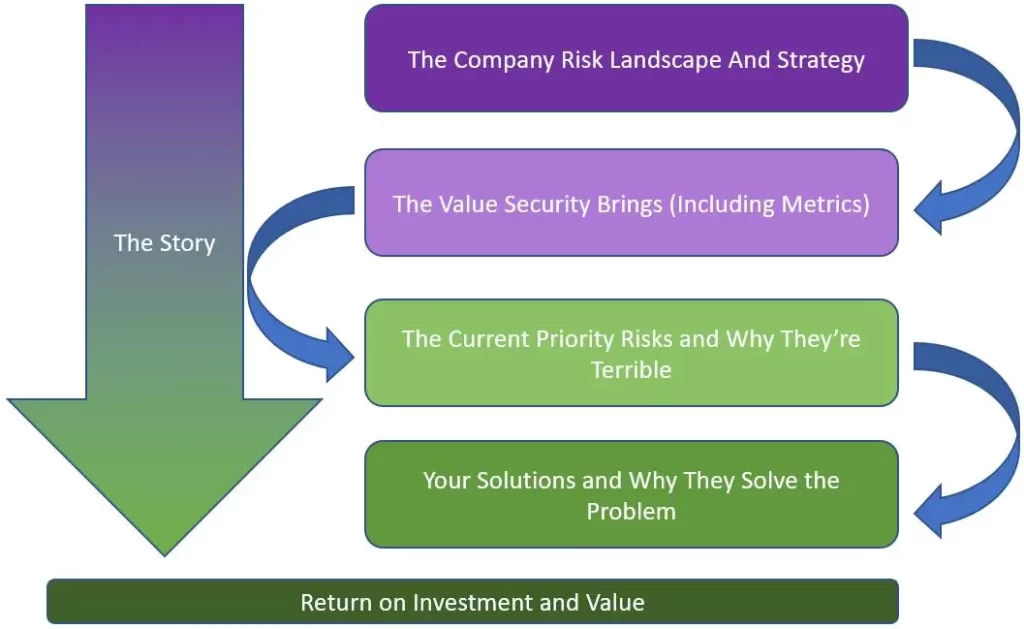
Step #1: Do Your Homework – Determine the Company Risk Landscape and Strategy
Key factors for determining the importance of security as it relates uniquely to your organization are:
- External risk exposure: Are you working with state and federal agencies? Is your organization dependent on partner manufacturing functioning 24/7 to meet demands? What risks does this pose to your security?
- Internal risk: Is turnover frequent? Is there technical debt?
- What business strategy or strategies have been laid out? What method will your organization use to get to success?
- Ultimately, what is your cybersecurity strategy? Does it align with your organization’s?
Guidance on this step of the process could form a 10,000-word guidebook but is beyond the scope of this post.
Know what your cybersecurity team will do that is in lock-step with your organization. This is the bedrock story of your budget pitch.
Step #2: Calculate Direct Value Added
1. Winning Revenue for the Business-
Think about areas where your cybersecurity team participated in direct revenue contributions: sales, contract renewals, winning RFPs, or the like.
Often, this means requirements/demands for compliance with ISO27001, SOC, NIST 800-53, PCI, GDPR, HIPAA, or related frameworks. How that works at your organization is the unique problem-solving value you and other technical teams bring to the table.
Consider the following multiples for levels of value the cybersecurity team brings to each contract won, retained, or renewed. These are called “Security Value Factors”:
- 5% – Contract involves multiple organizations, at least one business unit that your cybersecurity team does not support, or the contract does not directly rely on IT infrastructure, technical services, or software that your cybersecurity team supports.
Examples: manufacturing contracts where no IT exists in the OT environment, partnership-driven contract, and multi-phase projects where activities only fall under your cybersecurity “umbrella” for one phase.
- 10% – Contract scope is within the realm of your cybersecurity team, but is not directly dependent on output from IT or application services offered by your organization.
Examples: medical product or services contract where the medical production process includes IT services for the delivery chain.
- 25% Contract depends directly on IT and application services that your team oversees.
Examples: Colocation services, software services, data services.
- 100% Contract had a specific, explicit requirement for compliance with a cybersecurity framework in order to do business with them. If your team’s work is a keystone to the contract, consider 100% of the contract as value your team adds.
Look at every single sale the company has made, and do the following for each:
Total Contract Value (TCV, annualized) x Security Value Factor= Security Value of Contract
Add all those up, and you have the value that your security team has brought through sales.
2. Preventing significant operation or man-hour loss-
Having to mitigate IT and security problems takes time from teams other than your cybersecurity teams. Developers have to help release emergency bug fixes or operations needed to re-route workloads during a major disruption. These are much more subjective, but think about actual problems that dragged IT, developer, operations, marketing, etc. time away from strategic activities and forecasted plans in the last 12 months.
For each event, add up the approximate hour cost total.
Guess what the average salary of those involved are. If you have direct payroll data, that works too.
If you divide the average salary by 2000 hours (approximate working time for a year), then multiply by the hours lost to “distractions”, you have an idea of what you can prevent as the cybersecurity team, or at least reduce.
Further, hours spent fixing an unforeseen problem are hours taken away from achieving strategic objectives, so multiply the cost by two.
3. Operational gains in efficiency-
Your cybersecurity team may have worked to implement tooling and automation that can be leveraged across multiple departments to decrease man-hour costs for things like change management, system maintenance, communications, data flows, and infrastructure deployments.
You can repeat the above formula for this as well, but this is somewhat subjective.
4. Competitive distinction and brand development-
When your organization achieves compliance with frameworks or implements a new security program milestone, brag about it!
The business world attributes significant value to marketing already, and customers are increasingly sensitive to supply chain risks and third-party exposure. When your organization can demonstrate that it is a trustworthy partner, that’s value added by the security function.
This is the least objective measure but it is worth bearing in mind.
I hope you’re utilizing metrics to measure security performance. If you are, include those.
Don’t shy away from negative metrics! Dig into them and understand the true root causes.
Unless you sat at your desk with your feet kicked up, it’s highly unlikely that the blame is truly on the security team.
Step 3: Prioritized Risks And Why they Need Addressing
In keeping with your homework on your business’s strategy and the value your cybersecurity team brings to the table, identify the largest risks to your organization via the critical assets and processes your business depends on. Utilize risk or compliance assessments, penetration tests, your latest business impact analysis (BIA), and more to identify where the organization is most vulnerable.
These should be informed by, and directly tied to, your business’s strategic success factors.
Once more, the full discussion around painting the risk picture is beyond the scope of this post and highly unique to each organization.
Step 4: Your Solutions and Why They Solve The Problem
You’ve identified the strategy, the value the cybersecurity team has brought to the table, and the risks your organization faces.
Now let’s think about why you (as the leader of a cybersecurity team) need a budget:
- You know that there is a need for additional staff to manage infrastructure.
- Your staff are developing deep, specific knowledge and need their time freed up to facilitate strategic activities, so you want to hire more entry-level analysts.
- You have significant technical debt that could lead to a Southwest situation.
- A batch of needed vulnerability fixes are better handled by a third party familiar with the vulnerable platforms or systems.
- You’ve identified an automation opportunity and wish to purchase tooling that can reduce staff costs.
There are hundreds of other examples. Pick your top needs.
Attach these requirements as solutions to the problems and risks. Ideally, provide a “choice of yesses” to demonstrate your multi-faceted thinking and gain flexibility on budget. Gain conceptual agreement with your board or other leadership on this without showing a single dollar of cost.
The key messaging that has the highest chance of success in getting leadership buy-in is showing that the more expensive options result in higher chances of success, risk reduction, value protection, and/or value creation.
Example 1:
Problem: Significant single point of failure (SPOF) in critical manufacturing IT equipment that is vulnerable to attack.
| Option | Outcome |
| Isolate “blast zone” with stricter networking configuration | The risk of malicious actor threats is reduced, but SPOF remains |
| Implement redundant network flows | Risk of all-cause failure reduced, order throughput protected, still vulnerable to the original threat |
| Upgrade IT assets X, Y, and Z, including redundant routing | Allows network management backbone design, removes vulnerability entirely, eliminates the technical debt |
Value gained for all options:
- Overall manufacturing throughput risk reduction.
- Stress reduction for manufacturing teams and floor teams.
- Marketing opportunity regarding resilience to your organization
- $12.5m total value over the next 5 years.
Example 2:
Problem: Your company (AcmeCorp) has major compliance framework requirements from customers that may threaten existing contracts and the ability to win new ones.
| Option | Outcome |
| Halt work on X and reroute effort to gain compliance internally | Contract competitiveness protected, cost to other strategic and tactical efforts |
| Hire external assessment help and do remediation work at a cost of reducing work on X for Z hours/week for 8 months | Validated controls and remediation path, with implementation requiring work rerouting from AcmeCorp staff |
| Same as the previous option but include remediation and implementation assistance | Allows full compliance and contract competitiveness, validated controls and documentation, no cost to strategic or tactical operations |
Value gained:
- Existing contract revenue protected.
- Future earning opportunities increased with marketing around compliance.
- $8.5m revenue realization opportunity over the next 3 years.
Of course, you should always know your audience, and know how to tell the story of your past successes (or company failures), future opportunities, and how you can help the company “get there” with your security function.
This is the “story” part of Figure 1, and this is the thread you will run throughout all of this.
Think like an owner of the business would; ultimately, it boils down to ROI.
Find out more about how you can optimize your cybersecurity strategy today at https://www.ascentfoundry.com.
Bottom Line:
A well-planned cybersecurity budget is crucial to address the identified risks and problems effectively. By presenting your budget proposal as a solution to identified problems and risks, and demonstrating the potential value and ROI of your proposed solutions, you can gain buy-in from your organization’s leadership and secure the resources necessary to protect your critical assets and processes. Remember to tell a compelling story that highlights your team’s past successes and future opportunities, and always keep the ultimate goal in mind: protecting your organization and its stakeholders from the ever-evolving threat landscape.


