The IBM X-Force Threat Intelligence Index 2023 report has been released, revealing key insights and trends in cyber threats across the globe.
The IBM Security X-Force Threat Intelligence Index tracks new and existing trends and attack patterns – pulling from billions of data points from network and endpoint devices, incident response engagements and other sources.
The report offers useful information for CISOs, security teams, and business leaders to understand the strategies used by threat actors in their attacks, and suggests ways to proactively safeguard their organizations.
According to the report, backdoor deployments, which enable remote access to systems, were the most common type of attacker action, while phishing was the leading infection vector for the second year in a row, identified in 41% of incidents.
The study also found that while there was a slight decline in ransomware attacks, the time to execute them dropped 94% over the last few years.
The report provides actionable insights for CISOs, security teams, and business leaders to help proactively protect organizations from attackers. It is recommended that vulnerabilities be analyzed from multiple factors and prioritized accordingly to better understand an organization’s attack surface and risk-based prioritization of patches.
The report also suggests that in the current volatile landscape, businesses need to be armed with threat intelligence and security insights to stay ahead of attackers and protect their critical assets.
Table of Contents
Key Insights
- 2022 saw a surge in backdoor activity, with backdoors being deployed in almost a quarter of all incidents remediated. This rise in backdoor activity was attributed in part to a spike in Emotet, a multipurpose malware that contributed significantly to the increase in backdoor activity year over year. Despite this spike in backdoor activity, ransomware remained a significant threat, accounting for 17% of incidents and reinforcing the enduring threat that this type of malware poses.
- Extortion was the most common impact on organizations, with 27% of incidents resulting in extortion. Victims in the manufacturing industry accounted for 30% of incidents that resulted in extortion, as cybercriminals continued to exploit this industry, which has been particularly strained in recent years. Phishing remained the top initial access vector, identified in 41% of incidents, followed by exploitation of public-facing applications in 26%. Malicious macros fell out of favor, likely due to Microsoft’s decision to block macros by default, while malicious ISO and LNK files saw an increase in use as the primary tactic to deliver malware through spam.
- Phishing remains the leading infection vector, identified in 41% of incidents, followed by exploitation of public-facing applications in 26%. The report indicates that infections by malicious macros have fallen out of favor, likely due to Microsoft’s decision to block macros by default. Malicious ISO and LNK files were increasingly used as the primary tactic to deliver malware through spam in 2022.
- Cybercriminals Weaponize Email Conversations. Thread hijacking saw a significant rise in 2022, with attackers using compromised email accounts to reply within ongoing conversations posing as the original participant. X-Force observed the rate of monthly attempts increases by 100% compared to 2021 data.
- Legacy Exploits Still Doing the Job. The proportion of known exploits relative to vulnerabilities declined 10 percentage points from 2018 to 2022, due to the fact that the number of vulnerabilities hit another record high in 2022. The findings indicate that legacy exploits enabled older malware infections such as WannaCry and Conficker to continue to exist and spread.
- The war in Ukraine led to an increase in hacktivism and destructive malware. While the direst predictions of how cyber enables modern warfare haven’t come to fruition, there was a notable resurgence of hacktivism and destructive malware. IBM Security® X-Force® observed unprecedented shifts in the cybercriminal world, with increased cooperation between cybercriminal groups and Trickbot gangs targeting Ukrainian organizations.
Extortion Pressure Applied (Unevenly)
Cybercriminals often target the most vulnerable industries, businesses, and regions with extortion schemes, applying high psychological pressure to force victims to pay. Manufacturing was the most extorted industry in 2022, and it was the most attacked industry for the second consecutive year. Manufacturing organizations are an attractive target for extortion, given their extremely low tolerance for down time.
Ransomware is a well-known method of extortion, but threat actors are always exploring new ways to extort victims. One of the latest tactics involves making stolen data more accessible to downstream victims. By bringing customers and business partners into the mix, operators increase pressure on the breached organization. Threat actors will continue experimenting with downstream victim notifications to increase the potential costs and psychological impact of an intrusion – making it critical that businesses have a customized incident response plan that also considers the impact of an attack on downstream victims.
Thread Hijacking on the Rise
Email thread hijacking activity surged last year, with monthly attempts by threat actors doubling compared to 2021 data. Over the year, X-Force found that attackers used this tactic to deliver Emotet, Qakbot, and IcedID, malicious software that often results in ransomware infections.
With phishing being the leading cause of cyberattacks last year, and thread hijacking’s sharp rise, it’s clear that attackers are exploiting the trust placed in email. Businesses should make employees aware of thread hijacking to help reduce the risk of them falling victim.
Mind the Gap: Exploit “R&D” Lagging Vulnerabilities
The ratio of known exploits to vulnerabilities has been declining over the last few years, down 10 percentage points since 2018. Cybercriminals already have access to more than 78,000 known exploits, making it easier to exploit older, unpatched vulnerabilities. Even after 5 years, vulnerabilities leading to WannaCry infections remain a significant threat. X-Force recently reported an 800% increase in WannaCry ransomware traffic within MSS telemetry data since April 2022. The continued use of older exploits highlights the need for organizations to refine and mature vulnerability management programs, including better understanding their attack surface and risk-based prioritization of patches.
Additional findings from the 2023 report include:
- Phishers “Give Up” on Credit Card Data. The number of cybercriminals targeting credit card information in phishing kits dropped 52% in one year, indicating that attackers are prioritizing personally identifiable information such as names, emails, and home addresses, which can be sold for a higher price on the dark web or used to conduct further operations.
- North America Felt Brunt of Energy Attacks. Energy held its spot as the 4th most attacked industry last year, as global forces continue to affect an already tumultuous global energy trade. North American energy organizations accounted for 46% of all energy attacks observed last year, a 25% increase from 2021 levels.
- Asia Tops the Target List. Accounting for nearly one-third of all attacks that X-Force responded to in 2022, Asia saw more cyberattacks than any other region. Manufacturing accounted for nearly half of all cases observed in Asia last year.
IBM has compiled data from across the globe in the year 2022, to provide an insightful analysis of the global threat landscape, aiming to inform security experts about the dangers that pose the greatest risk to their respective organizations. To obtain a copy of the 2023 IBM Security X-Force Threat Intelligence Report, kindly refer to this link: https://www.ibm.com/reports/threat-intelligence/
Geographic trends
Europe saw a significant increase in backdoor deployments starting in March 2022, following Russia’s invasion of Ukraine. Backdoors accounted for 21% of cases in the region, with ransomware accounting for 11%. Remote access tools were identified in 10% of incidents. Of the impacts on clients, 38% were related to extortion, 17% resulted in data theft, and 14% were related to credential harvesting. Europe was the hardest-hit region in terms of extortion, representing 44% of all cases observed. The top infection vector used against European organizations was the exploitation of public-facing applications, accounting for 32% of all incidents. Professional, business, and consumer services and finance and insurance were the most-attacked industries, each representing 25% of the cases.
The United Kingdom was the most attacked country in Europe, accounting for 43% of cases.
Germany accounted for 14%, Portugal for 9%, Italy for 8%, and France for 7%. Spear phishing links decreased significantly, from 42% in 2021 to 14% in 2022, possibly due to better user awareness or stronger email security defenses.
The Asia-Pacific region saw manufacturing as the top-attacked industry at 48% of cases.
In the Asia-Pacific region, specifically Japan, the Emotet spike in 2022 occurred alongside Russia’s invasion of Ukraine, with spam campaigns identified across several industries, with most cases occurring in manufacturing and finance and insurance. Manufacturing was the most-attacked industry in this region, accounting for 48% of cases, followed by finance and insurance at 18%. Spear phishing by attachment was the top infection vector, accounting for 40% of cases, followed by exploiting public-facing applications at 22%. Deployments of backdoors were the most common action on objective, accounting for 31% of cases in the region.
North America’s most commonly attacked organizations were energy firms at 20% of cases.
In North America, there was a slight increase in the number of incidents, moving from 23% of all cases in 2021 to 25% in 2022. Energy firms were the most commonly attacked organizations, accounting for 20% of all attacks. Manufacturing and the retail-wholesale sector tied for second place at 14% each. Ransomware incidents accounted for 23% of cases, with 12% of cases being botnets. The top impact threat actors had was credential harvesting, accounting for 25% of incidents that X-Force remediated in North America. Data leak and data theft tied for second place at 17% each, with extortion accounting for 13% of cases.
Industry trends
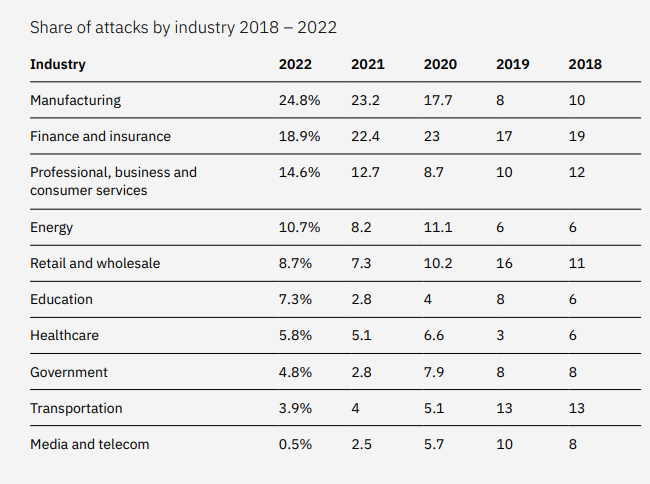
Manufacturing continues to be the most attacked industry, followed by finance and insurance, while backdoor attacks and spear phishing attachments remain the top observed actions on objective and infection vectors respectively.
Manufacturing Industry:
- For the second year in a row, the manufacturing industry was the most attacked, accounting for most X-Force incident response cases.
- Backdoors were deployed in 28% of incidents, beating ransomware, which appeared in 23% of cases.
- Spear phishing attachments and exploitation of public-facing applications were the top two infection vectors, each accounting for 28% of attacks.
- Extortion was the leading impact to manufacturing organizations, seen in 32% of cases.
- The Asia-Pacific region saw the most incidents in manufacturing at approximately 61% of cases.
- Manufacturing was the top-attacked industry, with a slightly larger margin compared to 2021.
- Europe and North America tied for second place at 14%, Latin American at 8% and the Middle East and Africa at 4%.
Finance and Insurance Industry:
- In 2022, finance and insurance organizations made up less than one in five attacks to which X-Force responded, earning second place, indicating a slight decrease over the past few years as other industries began to gain the attention of attackers.
- Backdoor attacks were the most commonly observed action on objective at 29%, followed by ransomware and maldocs at 11% each.
- Europe saw the highest volume of attacks on finance and insurance organizations with approximately 33% of all attacks, with Asia-Pacific in a close second place at approximately 31%.
- The top infection vector was spear phishing attachments, used in 53% of attacks against this sector.
- Exploitation of public-facing applications came in second place at 18% of attacks.
- Spear phishing links were the initial access vector at 12% of cases.
- Finance and insurance organizations tend to be further along in digital transformations and cloud adoption progress relative to other industries, making it harder for attackers to execute attacks against these organizations.
Professional, Business, and Consumer Services Industry:
- The professional services industry, including consultancies, management companies, and law firms, is the most attacked, accounting for 52% of victims in this segment.
- Business services, such as IT and technology services, public relations, advertising, and communications, represent 37% of victims.
- Consumer services, encompassing home builders, real estate, arts, entertainment, and recreation, account for 11% of cases.
- Professional, business, and consumer services experienced ransomware and backdoor attacks most frequently in 18% of cases each.
- The top two infection vectors were the exploitation of public-facing applications and external remote services, each accounting for 23% of attacks.
- Extortion was the most common impact in 28% of cases, with data theft, credential harvesting, and data leaks at 17% each.
- X-Force responded to 47% of cases in Europe, 33% in North America, 10% in Asia-Pacific, 7% in the Middle East and Africa, and 3% in Latin America.
Energy Industry:
- Energy organizations, including electric utilities and oil and gas companies, were the fourth-most attacked industry, representing 10.7% of attacks.
- The most common infection vector for attacks against the energy sector was the exploitation of a public-facing application, accounting for 40% of cases.
- Spear phishing links and external remote services were also common initial access vectors, each accounting for 20% of cases.
- Botnets were the most common observed action on objective at 46%, followed by backdoor attacks at 23% and ransomware at 8%.
- Extortion was the most common impact on energy organizations at 35% of cases, followed by data theft at 23% and credential harvesting at 19%.
- North America experienced the highest volume of attacks against the energy sector at approximately 67% of cases, with Europe and Asia-Pacific each experiencing approximately 16% of attacks.